What are blockchain transations “Hash Functions”?
The term “hash function” is derived from the French word “hacher” which means to “chop into small pieces”. Generically, a hash function converts input of any length to encrypted output of fixed length. Blockchain transactions hash functions are critical for encrypting transaction data on distributed ledgers. It maps variable sized transaction data to a standard hash format for processing across nodes in the blockchain network. Hashes create a fixed size bit string, the “hash value,” from any data set. The hash of data will be identical if the function runs on it again, allowing nodes to verify transactions using blockchain functions. You can validate data integrity by comparing its known hash to a newly generated one.
Hashing is also essential to blockchain management in cryptocurrency.
Hash Functions, in pills:
- Hash functions are mathematical functions that transform or “map” a given set of data into a bit string of fixed size, also known as the “hash value.”
- Hash functions are used in cryptography and have variable levels of complexity and difficulty.
- Hash functions are used for cryptocurrency, password security, and message security.
How do Hash Functions work:
Developers commonly use hash functions as data structures in computing systems to perform tasks like checking message integrity and authenticating information. While considered cryptographically “weak” because miners can solve them in polynomial time, hash functions are not easily decipherable.
Cryptographic hash functions add security features to typical hash functions, making it more difficult to detect the contents of a message or information about recipients and senders.
In particular, cryptographic hash functions ideally exhibit these three properties:
- They are “collision-free.” This means that no two input hashes should map to the same output hash.
- They can be hidden. It should be difficult to guess the input value for a hash function from its output.
- They should be puzzle-friendly. It should be difficult to select an input that provides a predefined output. Thus, the input should be selected from a distribution that’s as wide as possible.
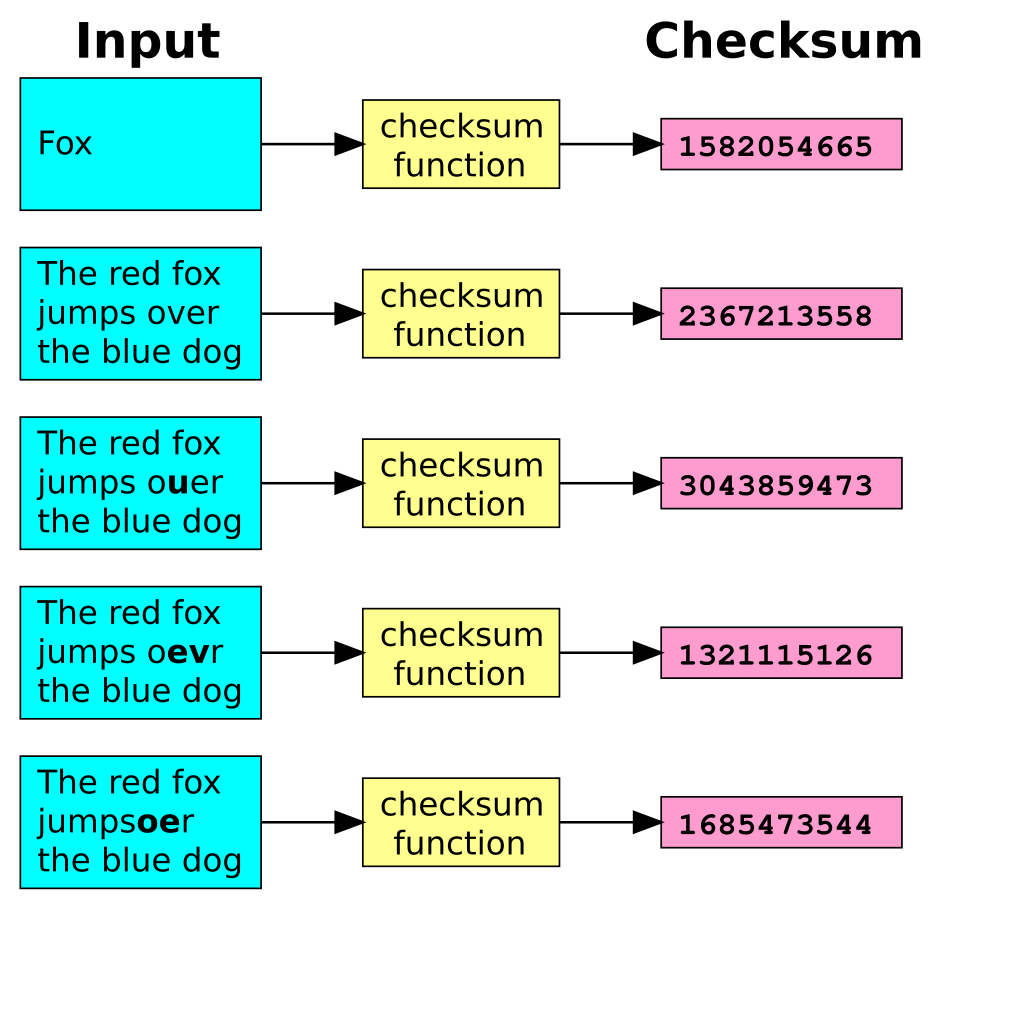
A hash function turns an input (for example text) into a string of bytes with a fixed length and structure. Miners call the output or value created a “hash value” or “checksum.” Any hash value that miners create from data using a specific hashing algorithm always has the same length and is one-way, meaning miners cannot reverse it.
Image by Wikipedia
Properties of hash functions
A hash function takes any input of arbitrary length and deterministically produces a fixed-length output, which miners refer to as the “hash digest.” Blockchains rely heavily on hash functions for generating cryptographic keys as well as hashing the transaction blocks.
General Properties:
- Fixed Length Mapping
- Deterministic
- Efficiently Computed
Cryptographic Properties:
- Preimage Resistance
- Collision Resistance
- Avalanche Effect
- Puzzle Friendliness
- Fixed Length Mapping
For input of any length, the function will always generate a fixed-length output. This property allows us to hash any file whether it is a text document, image or even a video file and get the output of the same length. There are multiple Hashing Functions out there like SHA-256, Keccak-256, etc.
For example, Bitcoin platforms largely rely on SHA-256: it takes in the input of any length and converts it into 256 bytes. This means that you can literally hash an entire movie into just 256 bytes.
Deterministic: For a given input, the output will always be the same. So, if I hash the word ‘hello’ using the SHA-256 hash function, then I will always get the same output.
So, mathematically, we can say for a given ‘X’, Hash(X) will always be the same.
Efficiently Computed: the hashing algorithm should be so efficient that you can compute hashes on an ordinary Laptop or PC using just your CPU cores. Not all hash functions are cryptographic hash functions, rather only the functions that exhibit the following cryptographic properties can be called “cryptographic hash functions”.
Preimage Resistance: given the output of the hash function (hash digest), you cannot determine the input. Therefore, if someone hashes a message and sends it to another, then even if they get a hold of the hash digest, they will not be able to decrypt what the original message was.
Mathematically, we can say that given Hash(X), you cannot determine X
Collision Resistance: for two distinct inputs, the output of the hash function should not be the same.
Mathematically, we can say that for 2 distinct inputs X1 and X2, Hash(X1) should not be equal to Hash(X2)
Avalanche Effect: it means that for a small change in the input, there will be a significant change in the output of the hash function.
Puzzle Friendliness: even if you get hold of the initial 200 bytes, you cannot determine the next 56 bytes from it. Having introduced hash functions, let’s now look at how miners use them in leading cryptocurrencies.
So, cryptographic hash function should be computationally efficient: it must be quick in performance to create the hash value. A hash function must be deterministic – it must produce the same output every time miners input the same value. It also must be pre-image resistant, meaning the output cannot reveal any information about the input.
Finally, the blockchain transactions hash functions have to be collision-resistant which ensures that it has to be impossible for two different inputs to produce the same output. It is the deterministic feature, pre-image resistance and collision-resistance that constitute the three most important properties of hash functions in the Bitcoin mining process.
Therefore a hash function has to be collision-resistant which ensures that it has to be impossible for two different inputs to produce the same output.
The usage in the mining process and the outcome
Miners bundle any block and include several transactions in it along with information on the previous block. This means, overall, that if someone wants to change the ledger or double-spend a transaction, they must change the hash in all previous blocks.
Miners must find a hash meeting the target difficulty to add a bundled block. Each block has a header listing its number, previous block’s hash, and a “nonce” holding a timestamp. The nonce varies input to the cryptographic hash function. It increases randomness in computations during mining. Miners change the nonce to modify the hash until below the difficulty target. This randomizes results across miners. Decentralization maintains through competition to find a valid hash first. The blockchain verifies the longest continuously validated chain cementing rewards. In summary, nonces and targets keep the blockchain open through distributed consensus.
The node then begins “hashing” the data by converting it into the hash value or “hash”, which always needs to contain a certain number of zeros. The node checks whether a hash meets the criteria of difficulty. The hash must start with the correct number of zeroes.
If the hash meets the criteria of difficulty, it is broadcast to the other miners in the network. The first miner to find a valid hash validates the block into a new block and gets rewarded the block reward and fees in Bitcoin.
If the hash does not meet the criteria of network difficulty, another nonce is selected and hashed. Miners probably have to generate many hashes with many nonces until they find a nonce that meets the difficulty. This is the repetitive and energy-intensive process known as Bitcoin mining which requires extensive computational power.
Hash functions constitute the backbone of the Proof of Work process.
Overall, without confirmation and production of the blockchain transactions hash functions, the technology would not be tamper-proof and inalterable and it would not be possible to prove who owned which amount of Bitcoin at what time.

Based in Zug, the platform is fully compliant with all Swiss laws related to financial intermediaries, banking, anti-money laundering, and organized trading facilities. Among its core values, there are innovative solutions through blockchain technology, which ensures security and liquidity.
EDSX is the first platform in Europe with primary and secondary markets for both institutional and retails. EDSX is a pioneering platform that employs the world’s leading technology to globally list security tokens in both primary and secondary markets, listing digital securities of real financial instruments to the public with a decentralized peer-to-peer exchange. Our goal is to fully engage every aspect of the financial revolution.
Do you have a question for us?
Send your query here:
[email protected]